Quantum computer-resistant
Quantum computer-resistant Public Key Infrastructures
By using innovative public key infrastructures within your organization, you ensure the integrity, confidentiality and authenticity of your transmitted information across applications and networks.
With QuantiCor’s highly secure solution “Q PKI”, our quantum computer resistant public key infrastructure, your communication channels are additionally protected against cyber threats from high performance computers, such as a quantum computer. In this way, you can achieve your desired level of IT security management and continue to make use of the full benefits of digitalization.
PKI: How to protect your communication channels
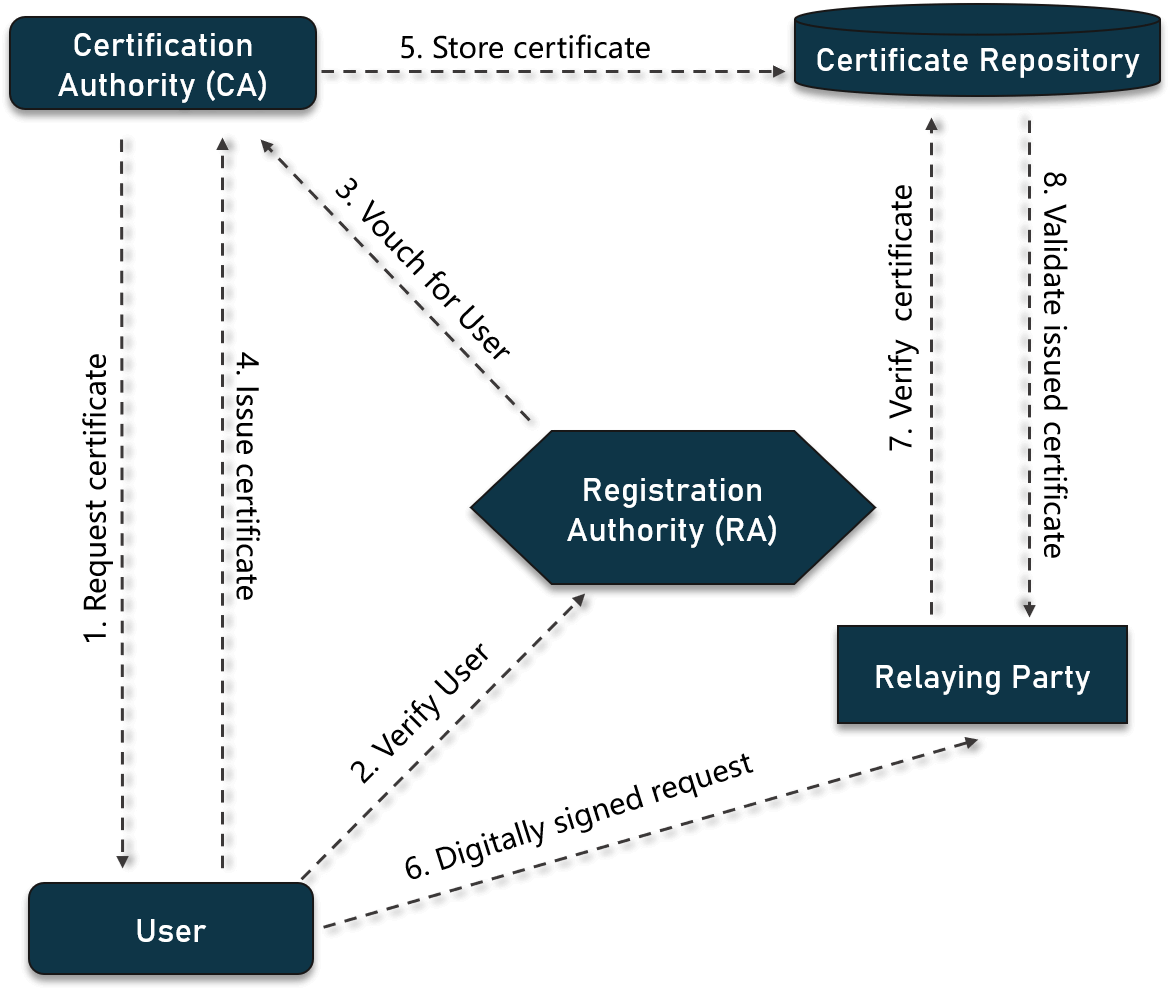
By using a so called Public Key Infrastructure (PKI) a security infrastructure is implemented in companies, through which service protected communication channels can be established. With the help of this technical component, the generation, management and verification of electronic certificates is achieved. As a result, it is possible to ensure trustworthy proof of electronic identities through a PKI.
For this purpose, a public key infrastructure comprises the following components:
- Certification authority for issuing and verifying digital certificates
- Certificate with the public key or public key information
By using a so called Public Key Infrastructure (PKI) a security infrastructure is implemented in companies, through which service protected communication channels can be established. With the help of this technical component, the generation, management and verification of electronic certificates is achieved. As a result, it is possible to ensure trustworthy proof of electronic identities through a PKI.
For this purpose, a public key infrastructure comprises the following components:
- Certification authority for issuing and verifying digital certificates
- Certificate with the public key or public key information
- Registration authority to verify the certification authority before issuing a digital certificate to the applicant
- Directories for storing the certificates (and their public keys)
- Certificate management system
- Registration authority to verify the certification authority before issuing a digital certificate to the applicant
- Directories for storing the certificates (and their public keys)
- Certificate management system
Features of Q‑PKI
- Secure identification of used or required keys, certificates and certification authorities
- Efficient and easy-to-use software for creating and managing PKI
- Enforce security policies for keys and certificates to maintain compliance
- Highly efficient protection of machine identities within your company infrastructure
- Fast exchange of compromised keys and certificates
- Protection against high performance computers, e.g. against quantum computer attacks, possible on request
With Q PKI, your communication channels and thus your data, information and infrastructure receive the urgently needed protection to ensure the future profitability of your company.
Would you like to dispense with a public key infrastructure when using your IoT devices in the future and thus save costs?
In this case take a look at our Quantum-IDEncrypt solution!