Quantum-Secure
Automotive security as a fundamental element within connected cars
Today, IT security poses enormous challenges for automobile manufacturers. The number of fully connected vehicles is increasing every year. Within these vehicles more and more complex software solutions are being developed, which at the same time offer a wide range of possible targets for cyber criminals. Due to the great competition within the automotive industry and the increasing pressure to create new innovations, the advantages of innovative solutions are always in the foreground. The aspect of automotive security is of secondary importance here and fatally gets more and more into the background.
From the perspective of Automotive Security, further developed security concepts are indispensable for car manufacturers and suppliers to be able to use all advantages of digitalization and thus new innovations in the fully networked vehicle efficiently and profitably.
To ensure the protection of vehicles, road traffic and passengers, software, data and functions must be protected against manipulation and access by unauthorized persons.
Automotive security as a fundamental element within connected cars
Today, IT security poses enormous challenges for automobile manufacturers. The number of fully connected vehicles is increasing every year. Within these vehicles more and more complex software solutions are being developed, which at the same time offer a wide range of possible targets for cyber criminals. Due to the great competition within the automotive industry and the increasing pressure to create new innovations, the advantages of innovative solutions are always in the foreground. The aspect of automotive security is of secondary importance here and fatally gets more and more into the background.
From the perspective of Automotive Security, further developed security concepts are indispensable for car manufacturers and suppliers to be able to use all advantages of digitalization and thus new innovations in the fully networked vehicle efficiently and profitably.
To ensure the protection of vehicles, road traffic and passengers, software, data and functions must be protected against manipulation and access by unauthorized persons.
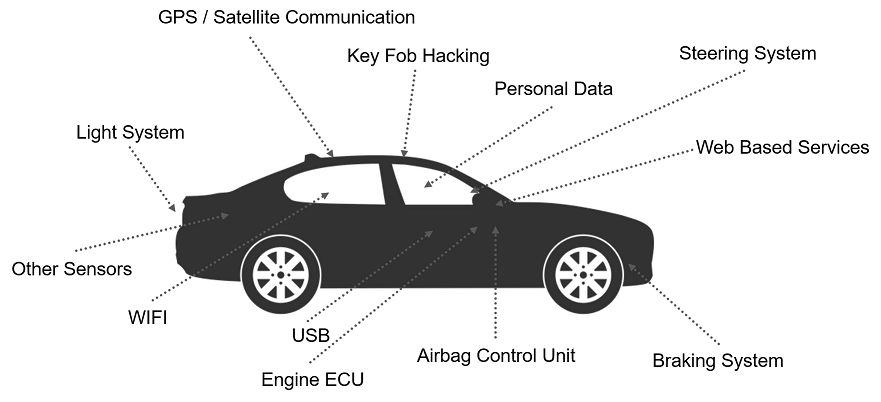
Vehicle networking requires a new generation of IT security solutions
One of the central mobility issues of this decade is the Connected Car. It is only a matter of time until all vehicles are permanently online and there are also continuous connections between the vehicle, the manufacturers’ back-end systems and other service providers.
This means that a vehicle ultimately acts like a data center and is thus also exposed to its cyber security threats. Since the buyers and passengers of a vehicle trust that the car manufacturer has closed any security gaps over the entire life cycle of a vehicle, an innovative IT security strategy is therefore essential. This strategy must be above current security standards, as cars are often in use for decades.
Common points of attack on IoT technologies in vehicles:
- Deficiencies in peer authentication
- Practical cryptographic manipulation
- Open gaps in endpoint integrity
- A lack of segmentation between critical and non-critical applications
- Disadvantages of software applications
- Gaps in the business logic
Vehicle networking requires a new generation of IT security solutions
One of the central mobility issues of this decade is the Connected Car. It is only a matter of time until all vehicles are permanently online and there are also continuous connections between the vehicle, the manufacturers’ back-end systems and other service providers.
This means that a vehicle ultimately acts like a data center and is thus also exposed to its cyber security threats. Since the buyers and passengers of a vehicle trust that the car manufacturer has closed any security gaps over the entire life cycle of a vehicle, an innovative IT security strategy is therefore essential. This strategy must be above current security standards, as cars are often in use for decades.
Common points of attack on IoT technologies in vehicles:
- Deficiencies in peer authentication
- Practical cryptographic manipulation
- Open gaps in endpoint integrity
- A lack of segmentation between critical and non-critical applications
- Disadvantages of software applications
- Gaps in the business logic