Post Quantum Security
The Achilles’ heel of digitization
How can passenger data be optimally used and are efficiently protected at the same time for the benefit of the passengers and the company? And how can digitalized work processes in the aerospace industry be effectively protected against cyberattacks?
Development cycles in the aerospace industry are much slower than in the automotive industry. Aircraft are often in use for decades. As a result, this industry often has to deal with difficult legacy systems, which can usually elude an IT security upgrade.
If we look at the on-board electronics of airplanes in particular, they are usually very complex and consist of vast amounts of code lines.
This leads to a high vulnerability or bugs in the code that allow access for manipulation or worse.
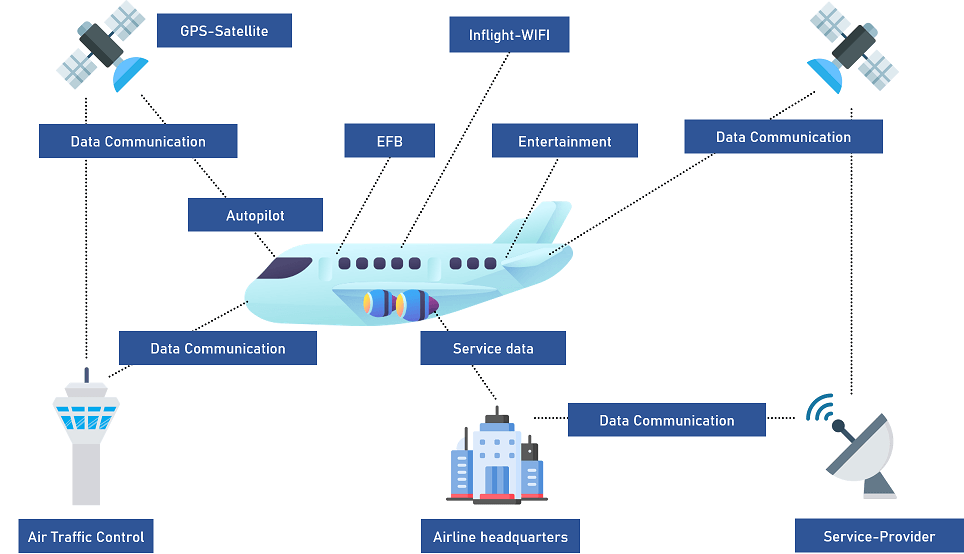
However, dangers do not only threaten from within the aircraft, because aircraft are networked with a wide range of communication services such as dispatch and flight control systems, whose signals can be disturbed (“jamming”) or manipulated (“spoofing”). The spectrum of possible targets for those attacks thus begins with the production facilities of aircraft manufacturers and ends with the networked IT infrastructures.
This example illustrates in an unpleasant way that insufficiently protected data and outdated IT infrastructures are the Achilles heel of these industries.
The Achilles’ heel of digitization
How can passenger data be optimally used and are efficiently protected at the same time for the benefit of the passengers and the company? And how can digitalized work processes in the aerospace industry be effectively protected against cyberattacks?
Development cycles in the aerospace industry are much slower than in the automotive industry. Aircraft are often in use for decades. As a result, this industry often has to deal with difficult legacy systems, which can usually elude an IT security upgrade.
If we look at the on-board electronics of airplanes in particular, they are usually very complex and consist of vast amounts of code lines.
This leads to a high vulnerability or bugs in the code that allow access for manipulation or worse.
However, dangers do not only threaten from within the aircraft, because aircraft are networked with a wide range of communication services such as dispatch and flight control systems, whose signals can be disturbed (“jamming”) or manipulated (“spoofing”). The spectrum of possible targets for those attacks thus begins with the production facilities of aircraft manufacturers and ends with the networked IT infrastructures.
This example illustrates in an unpleasant way that insufficiently protected data and outdated IT infrastructures are the Achilles heel of these industries.
QuantiCor, your strong partner in IT security
QuantiCor Security is a specialist in the field of security-critical infrastructures. Through years of research in the area of cross-generational IT security solutions, we are able to protect our customers in the best possible way against cyberattacks.
Our solutions are characterized in particular by the fact that they withstand the attacks of high performance computers, such as those of a quantum computer, can be easily embedded in IT infrastructures and also provide sustainable protection. In addition, we rely on crypto agility, regular updates and support in order to always equip your company with our new technologies and to protect you from new threats.
With us as a strong partner at your side, you don’t have to worry about protecting your infrastructures and can concentrate on your core competencies.